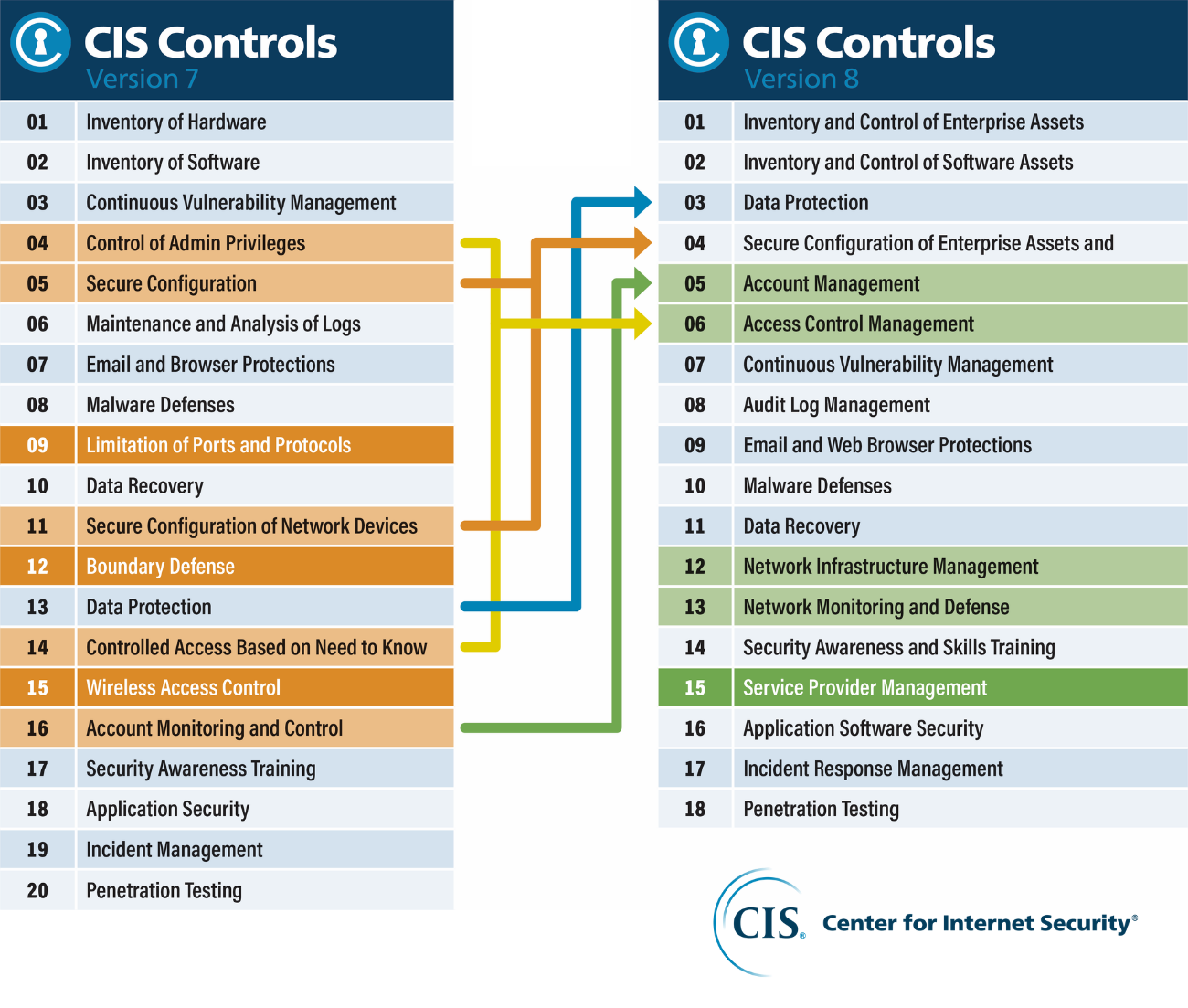
Implementing the CIS 20 Critical Security Controls: Building Upon Foundational Cyber Hygiene | Qualys Security Blog
Free Microsoft 365 Assessment Tool based on the top 20 Critical Security Controls from CIS and the Council on Cybersecurity | by Alex Fields | REgarding 365
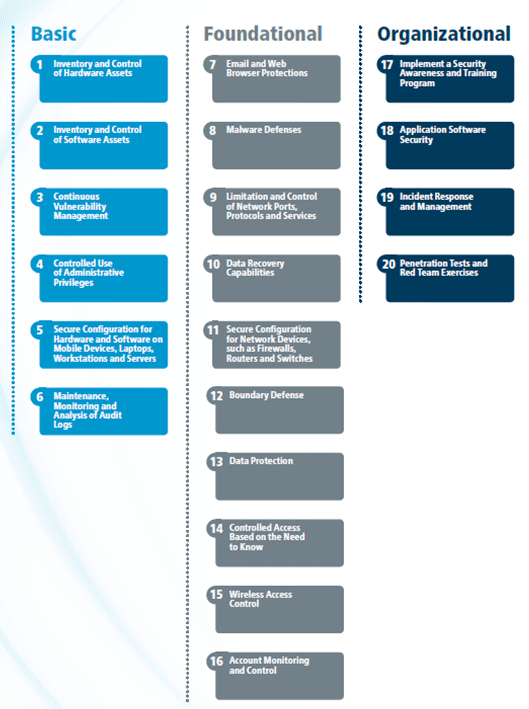
Transportation Management Center Information Technology Security - Executive Summary - FHWA Office of Operations

The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization | Qualys Security Blog
Free Microsoft 365 Assessment Tool based on the top 20 Critical Security Controls from CIS and the Council on Cybersecurity | by Alex Fields | REgarding 365
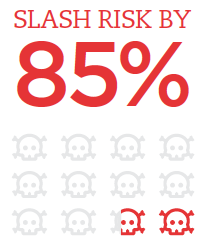
The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization | Qualys Security Blog